How Comodo NxSIEM Cloud works
Seven easy steps to security intelligence:
- Subscription
- Adding and Managing Customers
- Log Collection
- Classification and Indexing
- Retention and Search
- Analysis
- Real Time Correlation, Alerts and Incident Management
Subscription
You can sign up via Comodo Account Manager (CAM) and begin using NxSIEM Cloud immediately. No deployments, no softwares to install or databases to maintain. Our intiutive user interfaces enable fast learning and quick activation. Begin collecting logs, generating reports and correlating events just in minutes.
Adding and Managing Customers
After your account is created you can create your customers. Comodo respects your customer relationships and your customer's privacy. You can create and manage as many customers and devices as you need.
Log Collection
Agentless Collection:
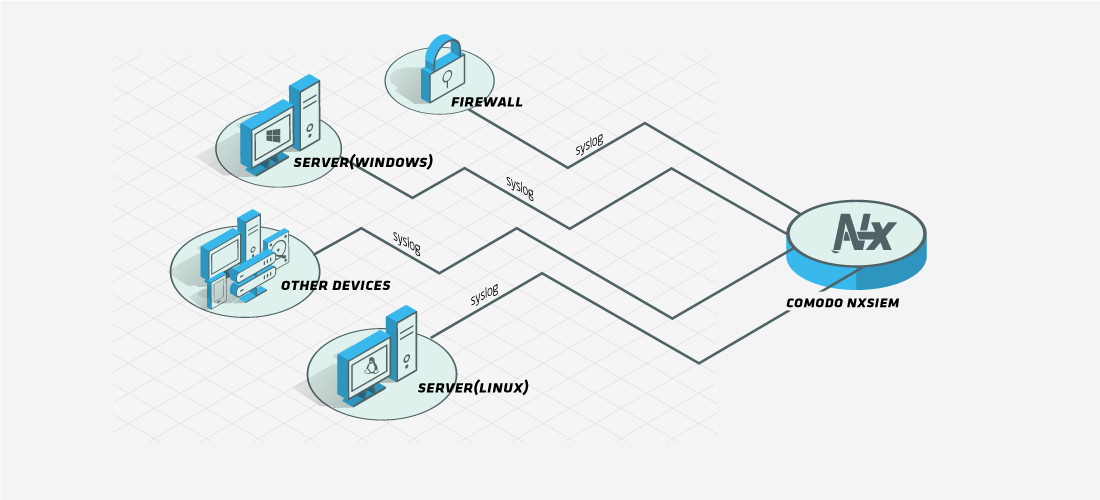
All devices and systems supporting syslog can be individually forwarded to our cloud servers if they have log forwarding enabled.
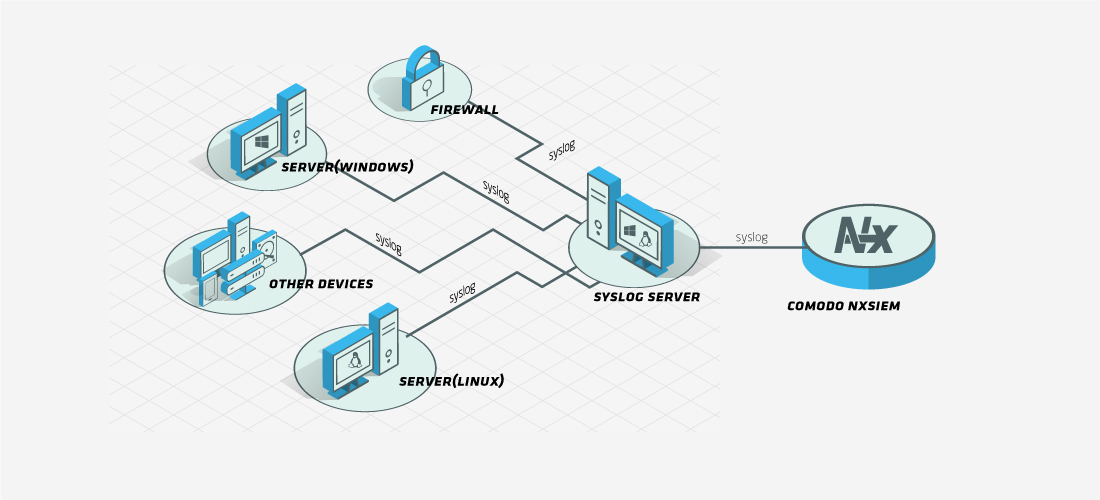
All logs collected on a syslog server can then be forwarded from that server without any agent deployment or configuration.
NxSIEM Sensor:
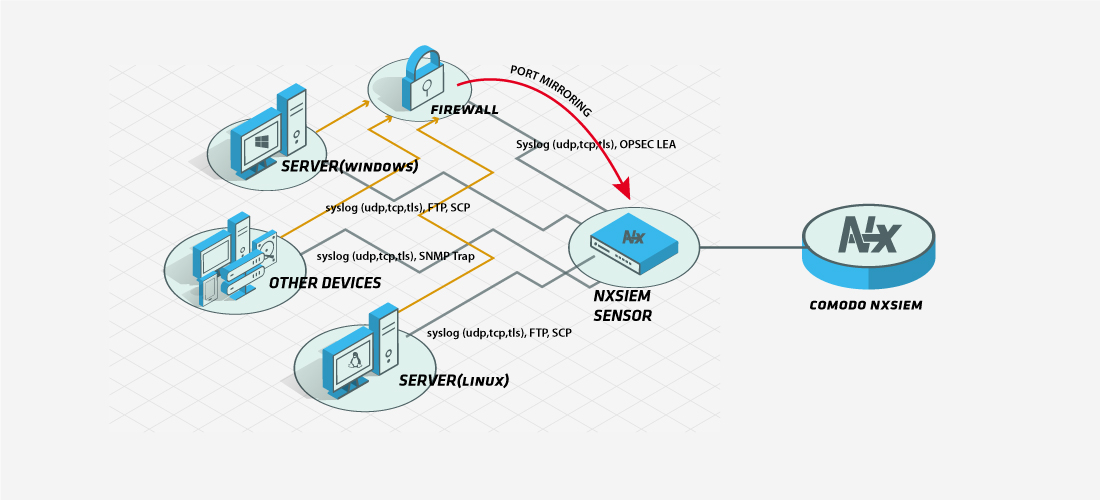
NxSIEM Sensor is a powerful virtual appliance that has log forwarding, network monitoring and intrusion detection capabilities. NxSIEM Sensor supports log encryption.
Collection by agents:
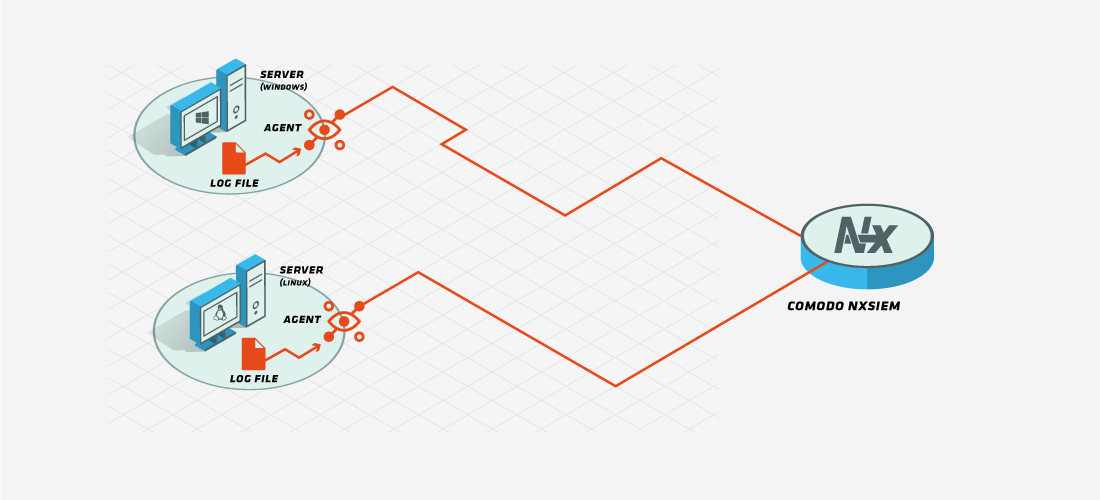
Deploying a flat file log collection policy to an agent on a machine, logs feeding the file can easily be collected and forwarded to our cloud servers.
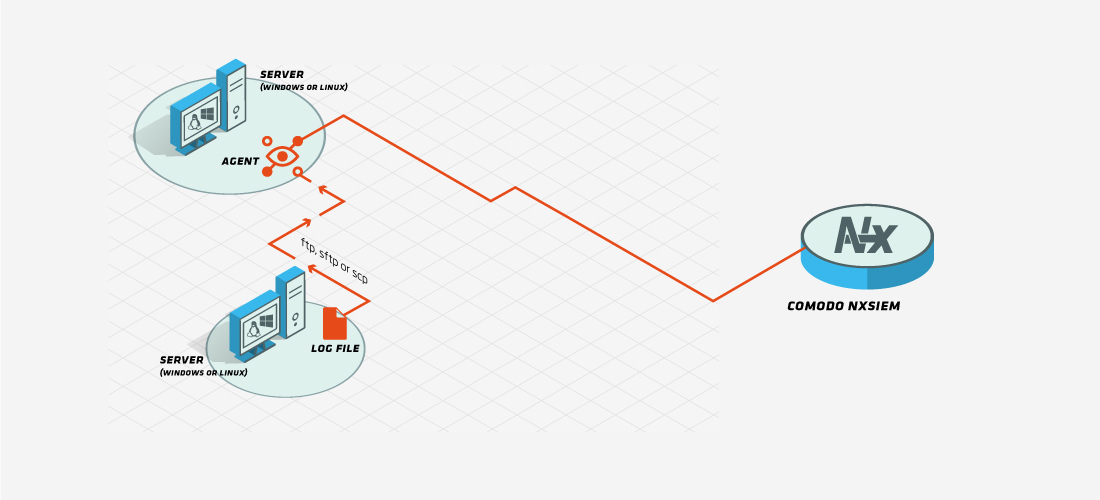
If the flat file resides on a remote machine, by granting access rights and using ftp, sftp or scp protocol, logs feeding the remote file can be collected from the machine that agent is deployed and forwarded to our cloud servers.
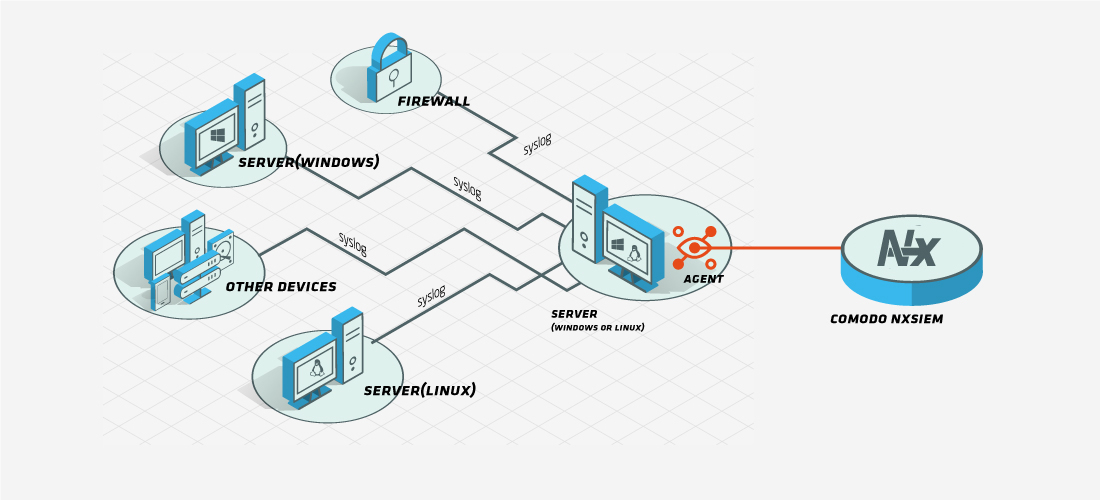
Agents can be configured to listen to syslog event feeds on a specific port. All events forwarded to this port from other devices or systems are collected and forwarded to our cloud servers.
Classification and Indexing
Collected logs are classified and enriched by complex classification and enrichment algorithms on our massively scalable cloud servers. Logs are indexed for fast search and drill down purposes in order to make details instantly available when an issue is detected.
Retention and Search
Leveraging big data for log retention and rapid search, enables more amount of logs to be ready for searching for longer terms. Log retention period and amount of log immediately ready for analyzing is very important for forensic analysis and compliance requirements. Big data architecture is the exact right choice for log retention and rapid search on especially multi-tenant cloud platforms where parallelism is crucial.
Analysis
You can analyze and visualize log data in various ways using Comodo’s SIEM Cloud capabilities. You can create custom dashboards and overview each customer's security situation, you can drill down on charts to the events, in order to see the underlying details for a specific condition by just one click and you can prepare long term reports and queries and conduct analysis about an attack providing specific details about the incident.
Real Time Correlation, Alerts and Incident Management
Comodo NxSIEM Cloud offers a very powerful real time correlation engine that supports complex event processing and event chaining in order to generate timely and valid alerts on complicated situations. Alerts and incidents are managed and using simple interfaces where escalation and evidence collection can be done easily with predefined overview dashboards to trace incidents globally or customer based fashion.

